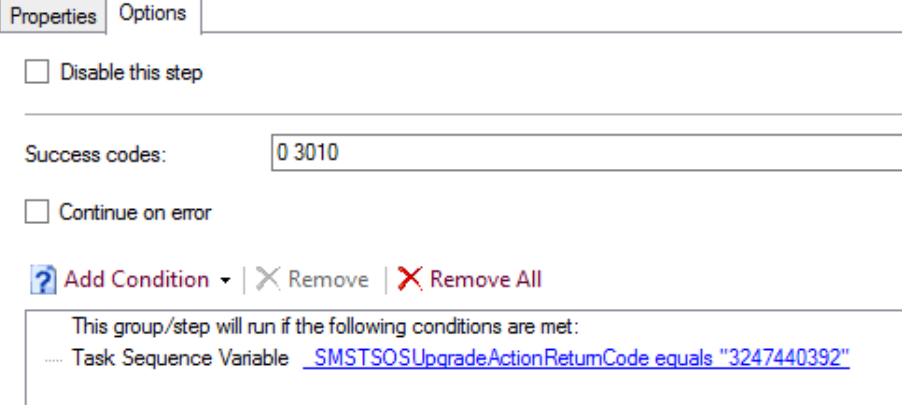
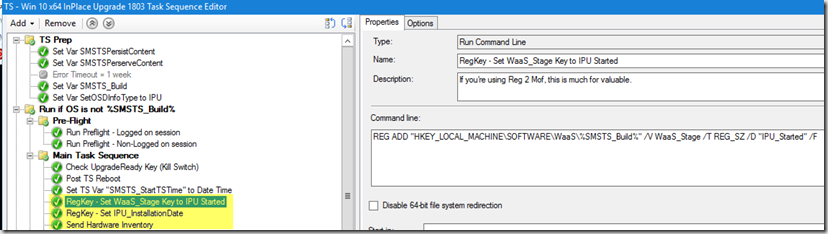
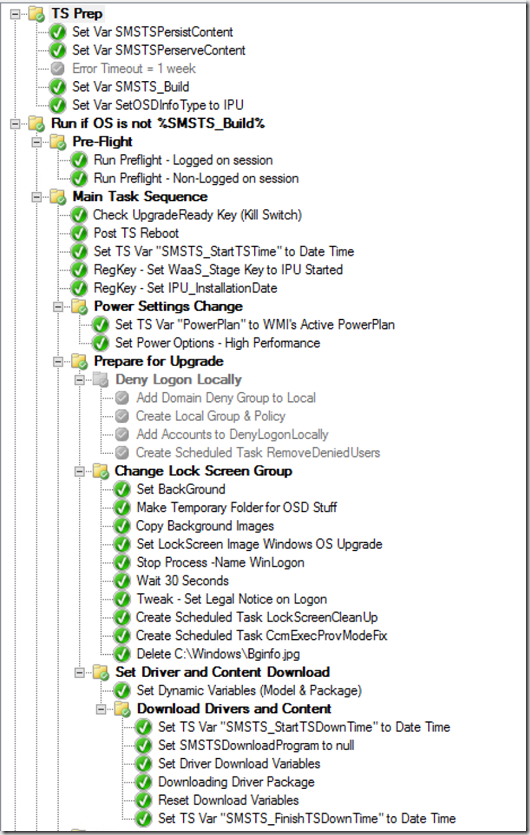
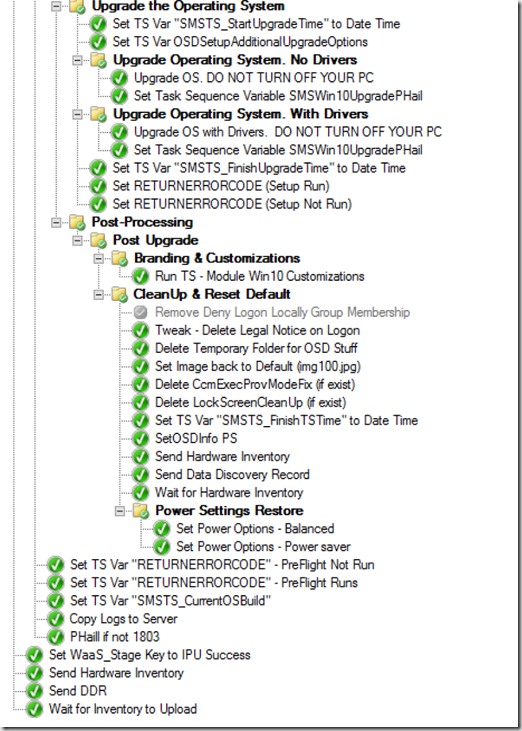
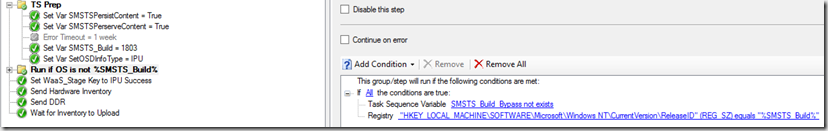
The CCMCache is pretty good at taking care of itself, but perhaps you have a reason to delete something specific, how do you do that in a supported way?
I have two scripts below, one that will just blow away ALL Software Updates in the cache, thoughts behind this, software updates should be installed within a couple weeks of being cached, after that, they are useless and never needed again, the other reason, if I’m upgrading to a new Windows 10 Build, I don’t need any of those old Windows 10 Software Updates in my cache anymore. (yes, you probably have others in there from office, etc, but hopefully you've installed them already, I admit, this isn't for everyone) Script Name:
Remove-CCMCacheSoftwareUpdateContent.ps1
Script 2, delete specific items based on ContentID. This is more for when you have a package / app you just want gone, perhaps you’re never going to deploy it again, or perhaps, someone accidently put a domain admin username & password in the script that’s now in the package sitting on all of our workstation ccmcache’s. Instead of dumping the entire cache, you can target a specific content and delete it. I also use this for deleting the Windows 10 Upgrade Media from the CCMCache after the upgrade. Normally you wouldn’t need to clean up after your task sequence, but if you precache your payloads into the ccmcache to speed up your actual deployment, then you’ll have that package contents just taking up space. Script Name:
Remove-CCMCacheContent.ps1
Flipside, Reasons to just leave it alone… once you fill up your CCMCache, it’s YOURS! You own that 20GB or whatever your CCMCache size is. No one can take that space away from you again. If you clear it out, sure, your machine might have more available free space, then the user steals it with cat videos, and guess what, when you need to cache that Adobe Software install, you can’t, not enough storage on the machine, if you would have just left the cache full, it would have cleared out what it needed at the time of the request, and pulled down the installer content.
How am I using them?
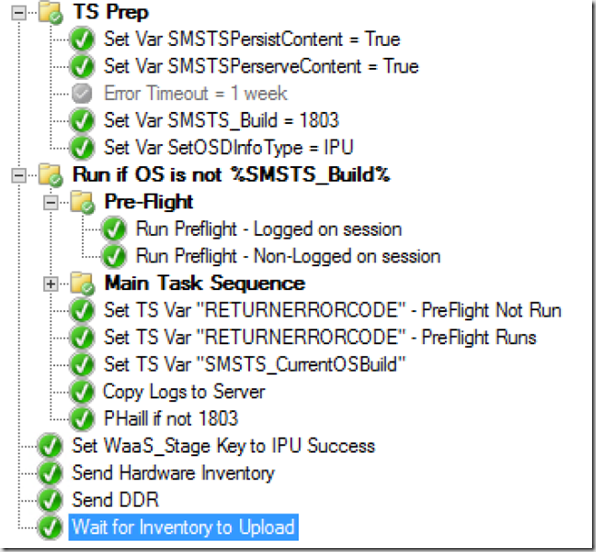
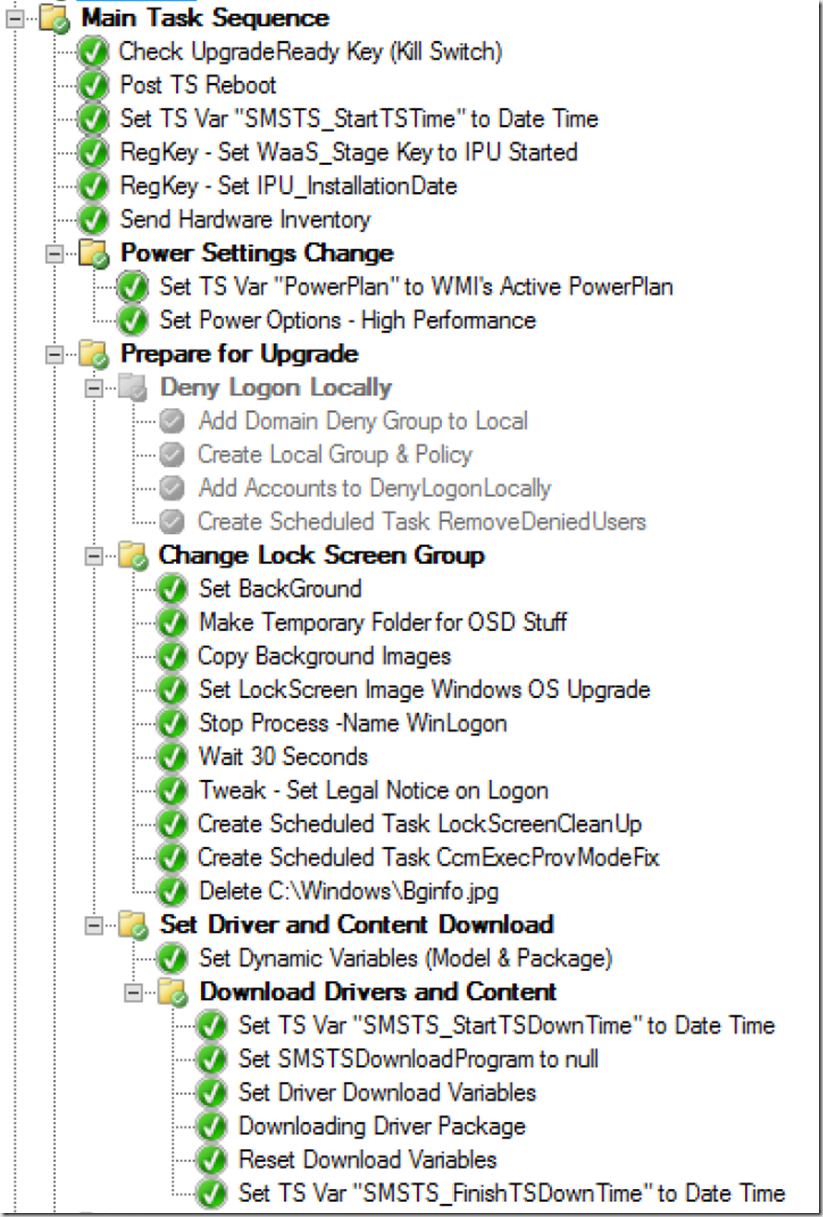
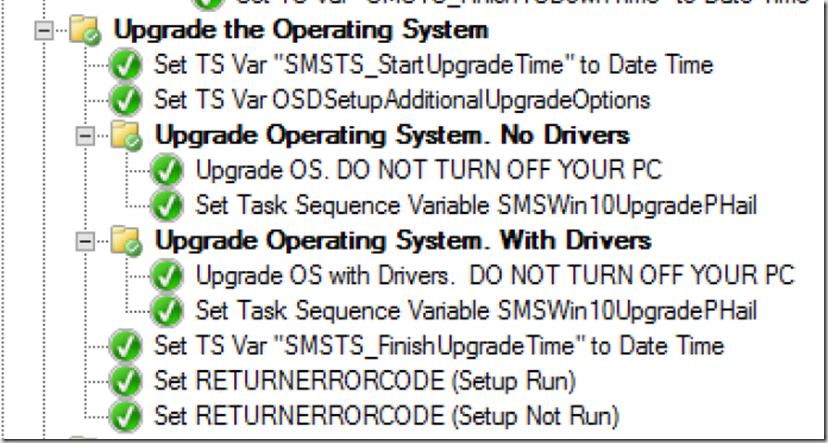
I have a script that will dump all of the Software Updates in the Cache, I use it in my Upgrade TS if after several other remediation's, still don’t have 20GB free space to start the Build upgrade.


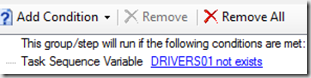
The other one, I have it clean up a couple packages at the end of the TS that are in the CCMCache from the PreCache TS:
Script is set to create a log in c:\windows\temp\ you can modify this to whatever you like.
Remove-CCMCacheSoftwareUpdateContent.ps1
<#
.SYNOPSIS
Delete Specified Item(s) From CCM Cache
.DESCRIPTION
Uses ContentIDs to identify (ALL SOFTWARE UPDATES) and purge content from the local ccm cache - Created by Gary Blok @gwblok
Partial Code borrowed from: https://gallery.technet.microsoft.com/scriptcenter/Deleting-the-SCCM-Cache-da03e4c7
Assist by Keith S. Garner @keithga1
.LINK
https://garytown.com
#>
$Logfile = "c:\windows\temp\Remove-CCMCacheContent.log"
# Connect to resource manager COM object
$CMObject = New-Object -ComObject 'UIResource.UIResourceMgr'
# Using GetCacheInfo method to return cache properties
$CMCacheObjects = $CMObject.GetCacheInfo()
# Delete Cache item
$CMCacheObjects.GetCacheElements() | Where-Object { $_.ContentID | Select-String -Pattern '^[\dA-F]{8}-(?:[\dA-F]{4}-){3}[\dA-F]{12}$' } | ForEach-Object {
$CMCacheObjects.DeleteCacheElement($_.CacheElementID)
Add-Content $Logfile -value "Deleted: Name: $($_.ContentID) Version: $($_.ContentVersion)"
Write-Host "Deleted: Name: $($_.ContentID) Version: $($_.ContentVersion)" -BackgroundColor Red
}Remove-CCMCacheContent.ps1
<#
.SYNOPSIS
Delete Specified Item(s) From CCM Cache
.DESCRIPTION
Uses ContentIDs to identify and purge content from the local ccm cache - Created by Gary Blok @gwblok
Partial Code borrowed from: https://gallery.technet.microsoft.com/scriptcenter/Deleting-the-SCCM-Cache-da03e4c7
Assist by Mark Godfrey @Geodesicz
.PARAMETER CachItemsToDelete
Comma separated values for the Content ID(s) of the cach item(s) to delete
.EXAMPLE
.\Remove-CCMCacheContent.ps1 -CacheItemsToDelete "PS100123","20eb8ec8-0b7e-4831-a5ae-95680b11e6b5","PS111197"
.LINK
https://garytown.com
#>
[CmdletBinding()]
Param(
[Parameter(Mandatory=$true,Position=1,HelpMessage="ContentIDs")]
[ValidateNotNullOrEmpty()]
[String[]]$CacheItemsToDelete
)
#$CacheItemsToDelete = "PS100002","20eb8ec8-0b7e-4831-a5ae-95680b11e6b5","decbb5fe-1cbc-4984-bbf2-e76347150135"
$Logfile = "c:\windows\temp\Remove-CCMCacheContent.log"
# Connect to resource manager COM object
$CMObject = New-Object -ComObject 'UIResource.UIResourceMgr'
# Using GetCacheInfo method to return cache properties
$CMCacheObjects = $CMObject.GetCacheInfo()
# Delete Cache item
$CMCacheObjects.GetCacheElements() | Where-Object {$_.ContentID -in $CacheItemsToDelete} | ForEach-Object {
#$CMCacheObjects.DeleteCacheElement($_.CacheElementID)
Add-Content $Logfile -value "Deleted: Name: $($_.ContentID) Version: $($_.ContentVersion)"
Write-Host "Deleted: Name: $($_.ContentID) Version: $($_.ContentVersion)" -BackgroundColor Red
}In Action:

as you can see, it deletes every version of the content id. AKA, if the client cached version 1 of the package, then you updated the package with a new file, the client could then download version 2 of the same package. Running this script will dump every version of that same package.
Feel free to use them however you want, I just tend to live in the Task Sequence world now, so that's how I use them.
Thanks to Mark Godfrey, Keith Garner & the PS Gallery, see actual scripts for more details.