Required Reading: KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932 - Microsoft Support
TLDR: GitHub: garytown/ConfigMgr/Baselines/CVE-2023-24932
Disclaimer: Before continuing, I've created all of this in a very short time with VERY LITTLE testing, so please, as with anything you're pulling from the internet, inspect and test before deployment. - Feedback Welcome!!
I've created a script that can be used for Configuration Manager Configuration Items & Intune's Proactive Remediation. The script will:
- Check System Event Log for ID 1035 [More Info]
- Test if 'System32\SecureBootUpdates\SKUSiPolicy.P7b' exist
- If Yes, Continue, if NOT, exit reminding you to apply May Patches
- Test if SKUSiPolicy.P7b has already been copied to the EFI partition (EFI\Microsoft\Boot)
- If Yes, skip the copy, if No, copy the file to the EFI Partition
- Update the Registry Key (Which resets after reboot)
- Trigger Reboot if Fix Event Log ID 1035 not exist after May Patches have been applied
- Feel free to remove this... just know it might take longer for fix to apply
Proactive Remediation
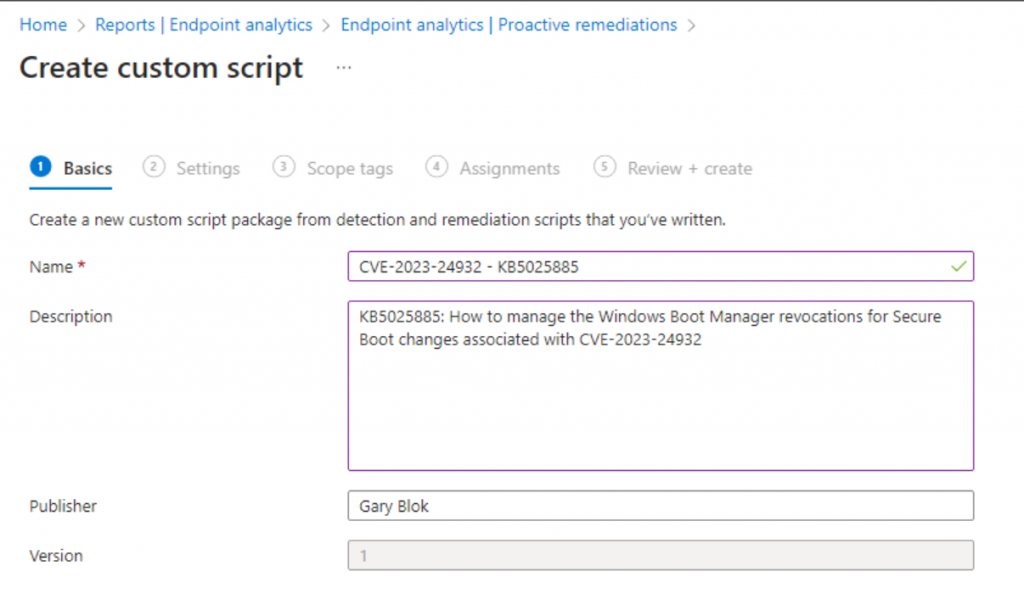
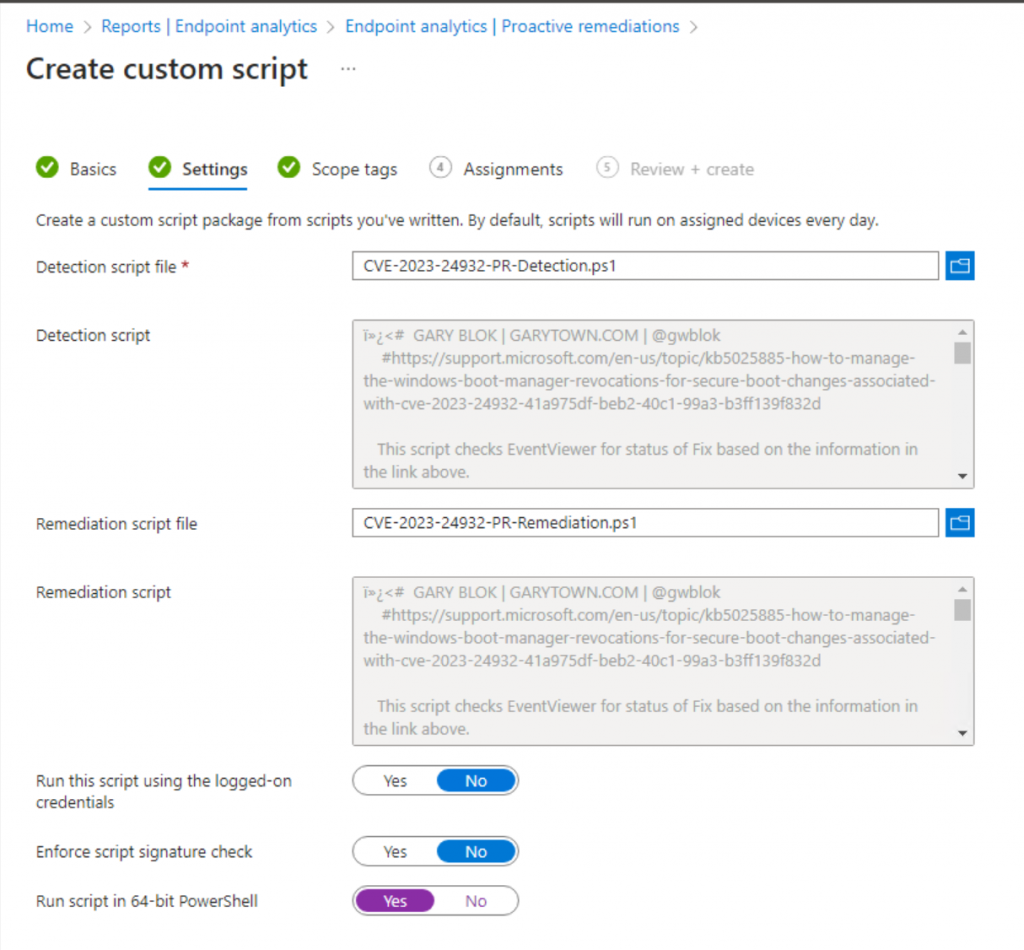
Then assign to your Windows Devices.
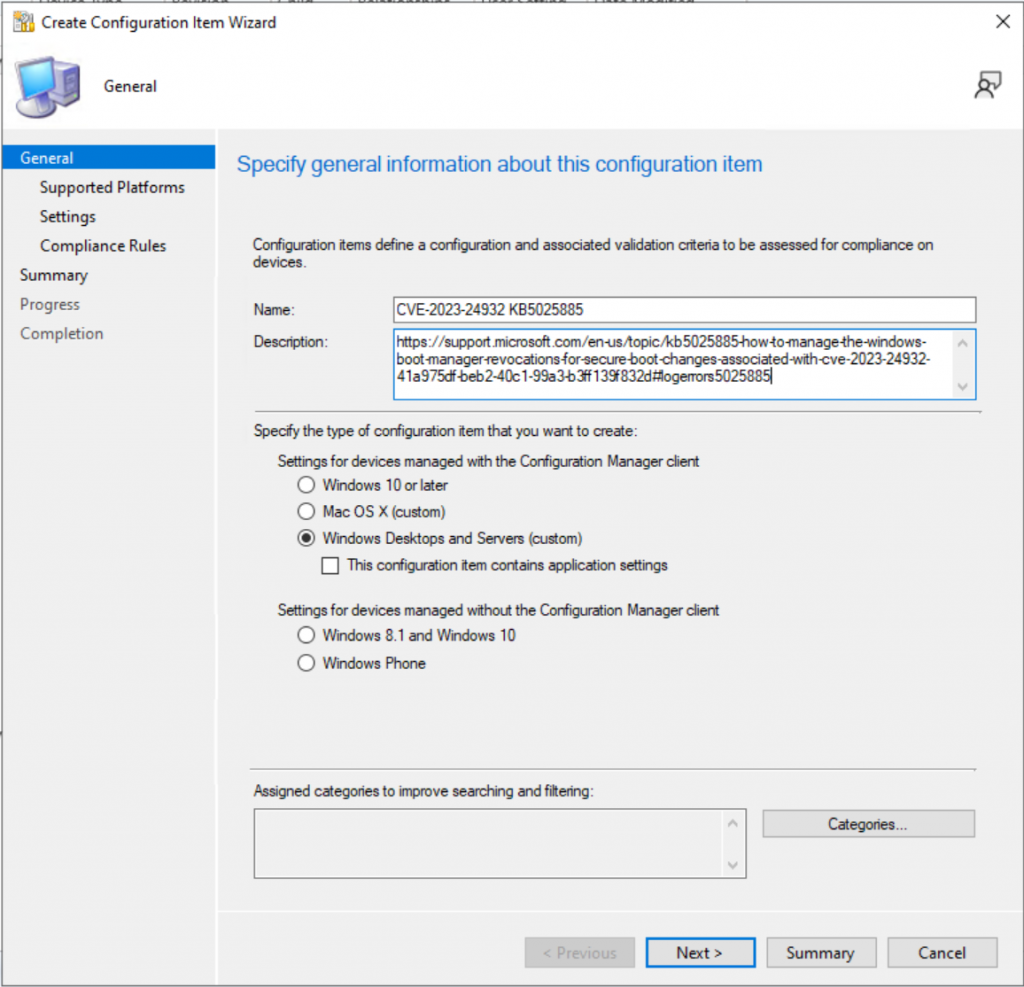
Configuration Baseline
Add information from the MS Website
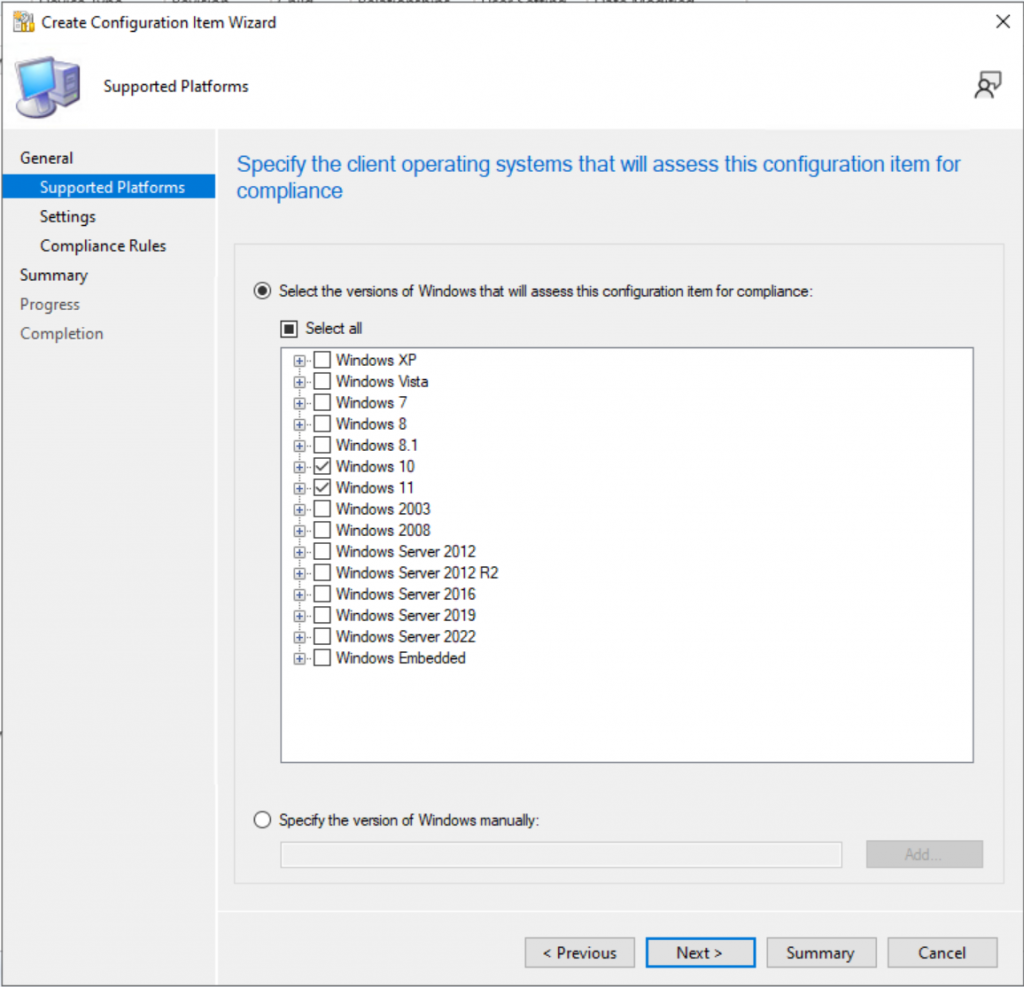
Check the Boxes for Windows 10 & 11
Set the CI Setting to Script / String, then add the scripts from GitHub
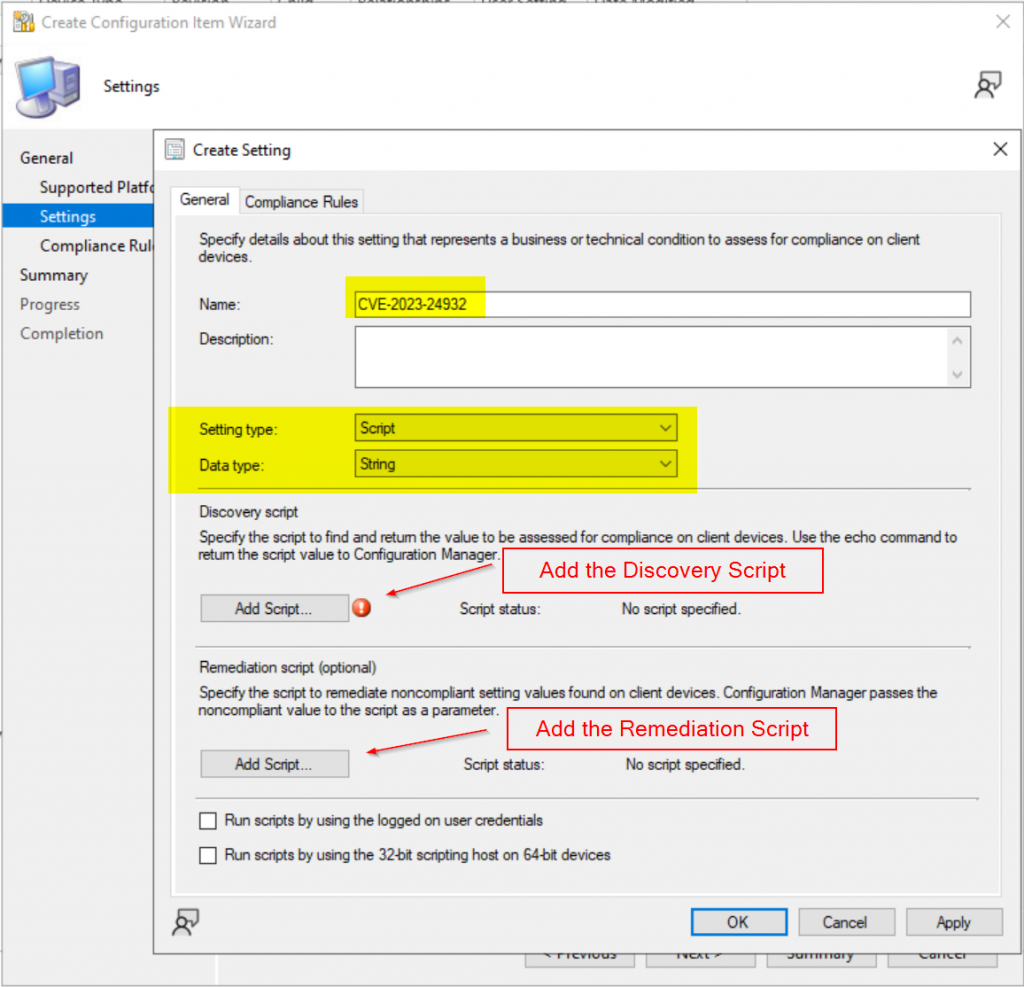
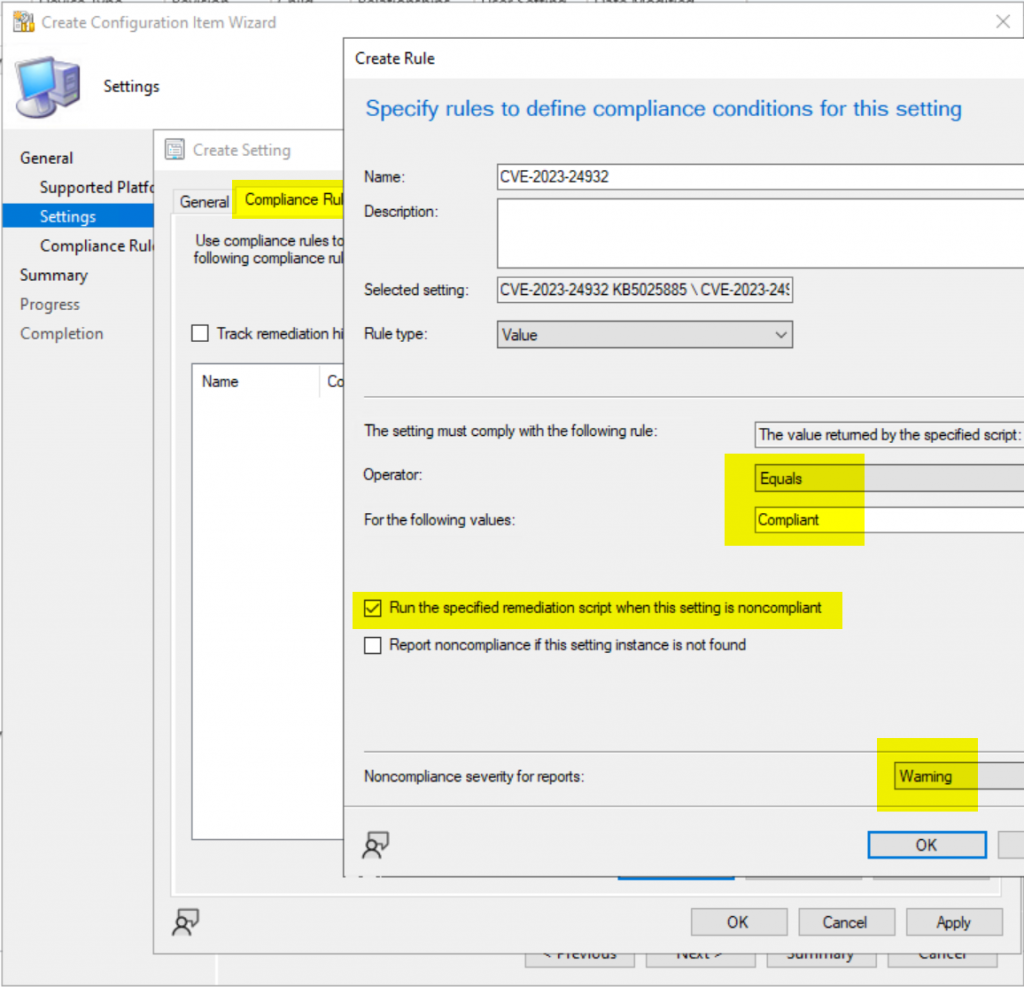
Create Compliance Rule, where Operator: Equals & value: "Compliant", Check the box for "Run the specified remediation script when this setting is noncompliant.
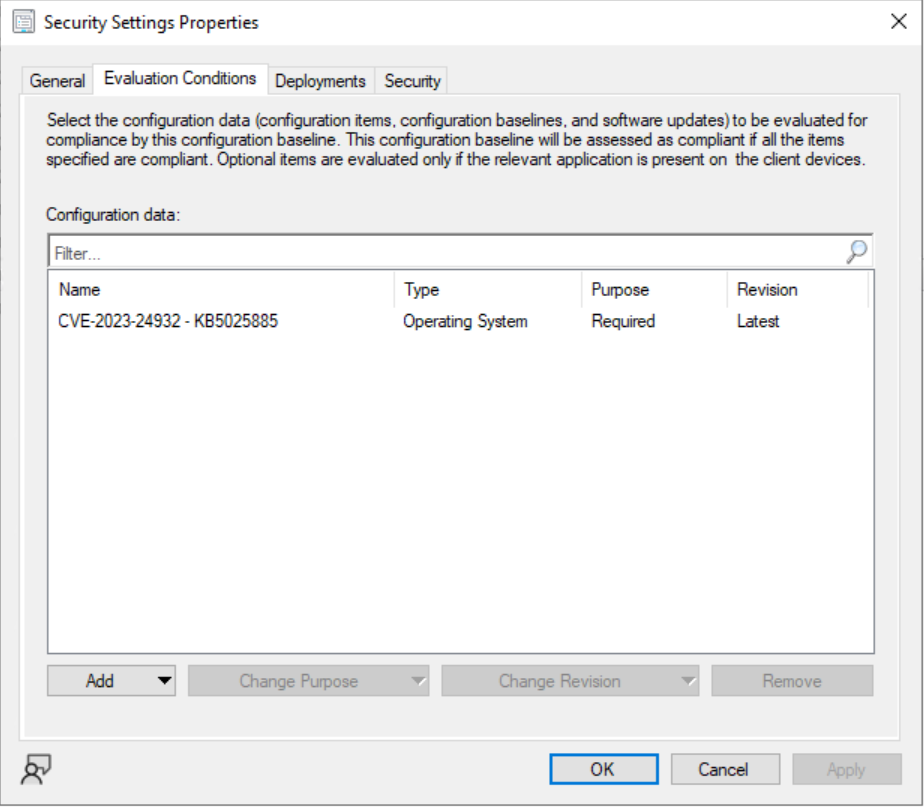
Add the CI to your Security Basline
Test & Deploy
GARYTOWN.COM